Researchers see spike in “out of season” IRS-impersonating phishing attacks
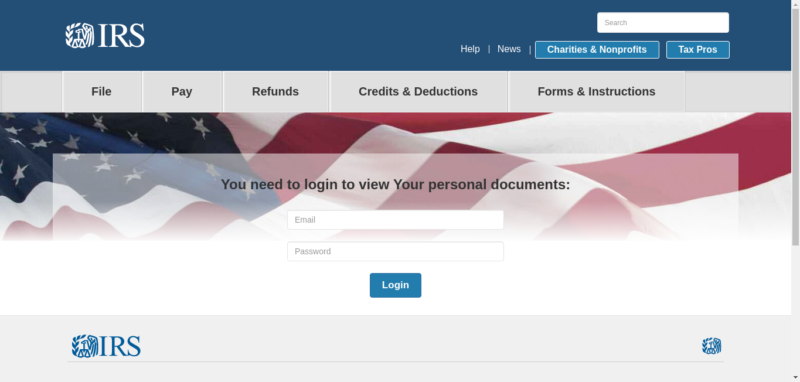

Enlarge / A fake IRS site used in a set of phishing campaigns observed by Akamai from August to October. (credit: Akamai)
Tax return scammers usually strike early in the year, when they can turn the personal information of victims into fraudulent tax refund claims. But members of Akamai's threat research team found a recent surge in "off-season" phishing attacks masquerading as notices from the Internal Revenue Service, targeting over 100,000 individuals. The attackers used at least 289 different domains hosting fake IRS websites—the majority of them legitimate sites that had been compromised. This wave of attacks came as the October 15 deadline for people who had filed for extensions approached.
According to a post by Akamai's Or Katz, the phishing campaigns kicked off in the second half of August, with the majority of victims targeted between August 22 and September 5. But the campaigns continued to be launched into early October. Each of the fake websites used visually identical HTML pages, but used randomly generated style tags and other content in an attempt to throw off signature detection by security software.
Most of the domains were active for under 20 days. However, a significant number of them remained active after a month—undetected by the owners of the sites. "The lack of maintenance on legacy websites, as well as the challenges of patching and removing injected content, explains the duration over which phishing pages can remain active," Katz wrote.
Comments
Post a Comment